Видео ютуба по тегу Using Kdf For Security

Asymmetric Encryption - Simply explained

Bitwarden Tutorial | The Full Beginners Guide

PRFs explained: Transforming Secrets into Infinite Keys - Pseudo Random Functions

MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication Codes

Bitwarden Tutorial | How to use Bitwarden in 2025?

The Most Important Bitwarden Setting You Never Heard Of

USENIX Security '23 - Multi-Factor Key Derivation Function (MFKDF) for Fast, Flexible, Secure, &...

Hackers Targeting Bitwarden Vaults | Easy Steps to Protect Your Passwords

What Is Key Derivation? - CryptoBasics360.com

Bitwarden Passwords At Risk? | A Security Expert Explains

Demystifying Key Stretching and PAKEs

Hashing Passwords Safely using a Password Based Key Derivation Function (PBKDF2)

The 8th BIU Winter School: More on Implicit Authentication; Key Derivation - Hugo Krawczyk
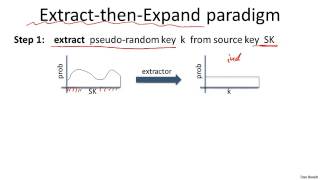
8 1 Key Derivation 14 min
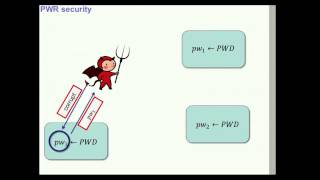
Multi-instance Security and Its Application to Password- ...

USENIX Security '24 - MFKDF: Multiple Factors Knocked Down Flat

PW20 Password Based Encryption Using IO Hardness Greg Zaverucha

Secure Element or TPM or HSM : Hardware Security in your Project Using wolfSSL and wolfBoot in 2022

KDF security and environment conference

#20 - Introduction to Encryption: Understanding Security Algorithm Use Cases